How To Build A Leading Detection And Response Engineering Practice | Forrester
Cyber Security |
Most SOCs Struggle With Their Core Mission: Detection and Response
Forrester’s Security Survey 2022 reveals that the primary challenge for security decision-makers is the ever-evolving nature of IT threats. The security operations center (SOC) and its analysts are pivotal in detecting and mitigating attacks that surpass preventive measures. However, many security operations (SecOps) teams struggle, having evolved out of necessity into a loosely structured discipline focused on responding to alerts of potential attacks.
Forrester defines security operations as The practice within an enterprise dedicated to hunting for, detecting, investigating, and responding to cyberattacks.
In many organizations, the SOC is still an ad hoc team of IT professionals stepping into the realm of cybersecurity. SecOps teams often face several challenges:
- Overwhelmed by Alert Management: According to Forrester’s 2022 data, one-quarter of security decision-makers at future-fit firms cite the excessive time spent on tactical activities as a significant IT security challenge. SOCs are burdened by the constant need to address current threats, leaving little time to strategize for future threats. This workload only increases with the expansion into cloud infrastructure and the influx of data from various sources. Matt Peters, chief product officer at Expel, states, “The average SOC is a bad place to work because it is basically a click factory.”
- Insufficient Staff and Continuous Rule Building: Finding and retaining detection engineers, threat hunters, and threat intelligence managers is challenging. As Keith McCammon, chief security officer at Red Canary, puts it, maintaining and updating detection coverage is a continuous effort, akin to running on a hamster wheel. Many tools offer out-of-the-box detections, but ongoing detection, rule creation, and tuning are often neglected due to a lack of process, discipline, and staffing.
- Talent Burnout Pipeline: Employee burnout in SOCs is often driven by a lack of personal satisfaction and enrichment. In most SOCs, level one (L1) analysts triage alerts and pass them to level two (L2) analysts for deeper investigation and response, limiting L1 analysts’ learning and job satisfaction. Without exposure to the full lifecycle of alerts, L1 analysts find it hard to advance in their careers and feel a lack of accomplishment. This structure leads to promotions based on certifications, which require analysts to invest time and money outside work, further diminishing their connection to the organization. Employees unable to grow will eventually leave for other opportunities.
- Product Proficiency Over Core Security Principles: Forrester’s 2022 data indicates that 52% of global security decision-makers who face challenges due to a lack of skilled security employees cite a deficiency in technical skills. Even those with technical skills are often trained on specific products like Splunk, CrowdStrike, or QRadar, rather than on fundamental security principles. The SOC expects entry-level security analysts to apply security principles without adequately teaching them these concepts.
In summary, many SOCs face significant challenges in fulfilling their primary mission of detection and response due to an overwhelming volume of alerts, insufficient staffing and processes, employee burnout, and a focus on product proficiency rather than core security principles.

Transform the SOC by Adopting Developer Approaches with the DR-DLC
The SOC is at a crucial juncture similar to the one software development faced years ago. It’s grappling with overwhelming data (big data and log management), struggling to innovate and update monolithic processes (detections and incident response), and lacks ownership beyond initial deployment (content management). The software industry responded to these challenges by transitioning from building monolithic software with a waterfall methodology to adopting microservices and agile practices. The SOC can benefit from these lessons by applying them to detection and response engineering — the engineering-centric capability responsible for creating new detections and automating response workflows.
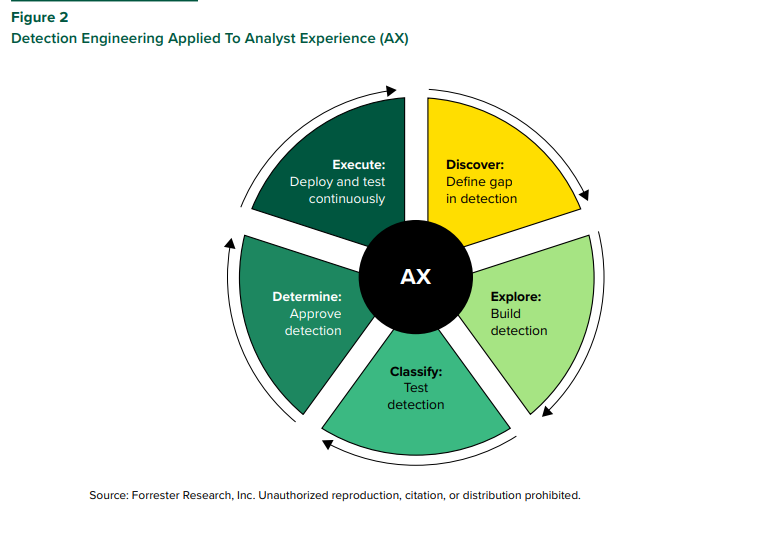
Applying Software Development Principles to Detection and Response Engineering
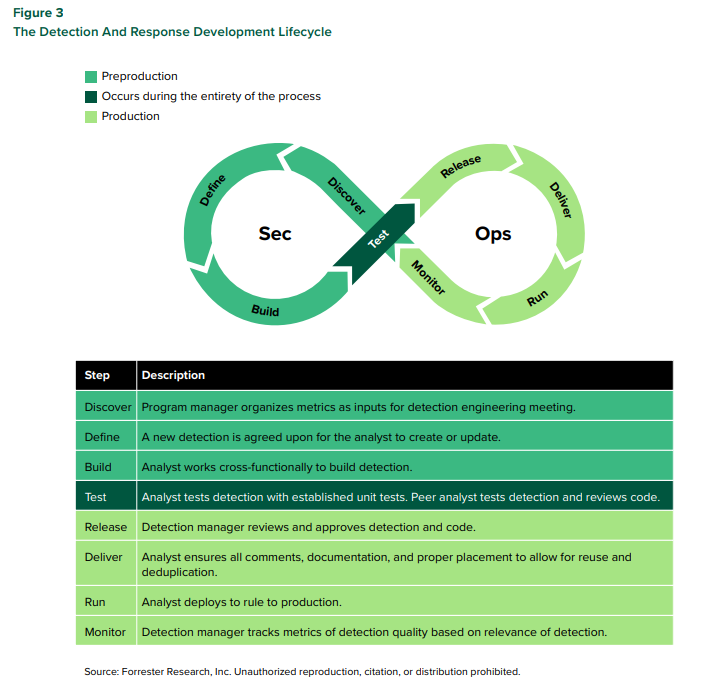
Frameworks like the software development lifecycle (SDLC) and Forrester’s Modern Application Delivery (MAD) Model provide a foundation for enhancing development processes with a focus on business value. These models can be adapted to detection and response engineering to accelerate the creation, tuning, and retirement of rules and analytics. To leverage the benefits of the SDLC, structure your detection and response engineering program around the detection and response development lifecycle (DR-DLC). The DR-DLC is an SDLC-based framework tailored for detection and response engineering, emphasizing business value through a tight cycle process from ideation to delivery and continuous testing.
Keith McCammon, Chief Security Officer at Red Canary, advises, “Focus first on detection and response. Operationalize threat intelligence through engineering-driven detection that is repeatable, scalable, and testable. Testing is critical and often overlooked — you should test and measure everything you can, from your data pipeline to your team’s response.” This framework helps your team establish a consistent and timely build process that includes ideation, design, build, test, release, and continuous monitoring.
Continue reading and download the report to learn how to build a leading detection and response engineering practice.
The Table of Contents of “How To Build A Leading Detection And Response Engineering Practice” Report:
- Most SOCs Struggle With Their Fundamental Mission: Detection And Response
- Transform The SOC By Embracing Developer Approaches With The DR-DLC
- Enhance Detection Engineering With Agile + SecOps
- Supplemental Material
Number of Pages:
- 12 pages
Pricing:
- Free






