Guides
Guide to CMS Security Best Practices & Protocols | Brightspot
Executive Summary Your CMS is essential to connecting with readers, employees, and partners. However, it also represents a prime target for cybercriminals, posing a significant vulnerability to your business. This eBook provides detailed CMS cybersecurity best practices to help secure your organization. We explore the rise in cybercriminal activity, its impact on content management systems, …
Guides
10 Code Signing Best Practices | Code Signing Store
Code Signing Shields Your Hard-Earned Work… Neglecting proper code signing and mishandling private keys can expose you to risks ranging from malware infiltrations to installation hitches for your clients. Continue reading to discover 10 practical code-signing best practices to maintain your organization’s security. Every code segment, container, app, and executable you craft should prioritize security …
Guides
Demystify Budget Priorities Crucial For A Resilient Cybersecurity Strategy | Forrester
Amidst the current uncertain macroeconomic landscape, security and risk (S&R) leaders require actionable advice for overseeing both existing expenditures and incoming budget proposals. This guide, driven by data analysis, offers spending benchmarks, valuable insights, and recommendations aimed at helping you maintain financial discipline while effectively addressing the most pressing risks confronting your organization. Constrained Economic …
News
Instagram Adds Restrictions on Diet and Cosmetic Surgery Content & Ads
Instagram has made restrictions that prevent users under the age of 18 from seeing certain content pushing weight loss products and cosmetic procedures. As concerns have been raised about the impact that diet, detox and cosmetic surgery content can have on young people, their mental health and body image. Instagram new restrictions also include removing …
Indicators
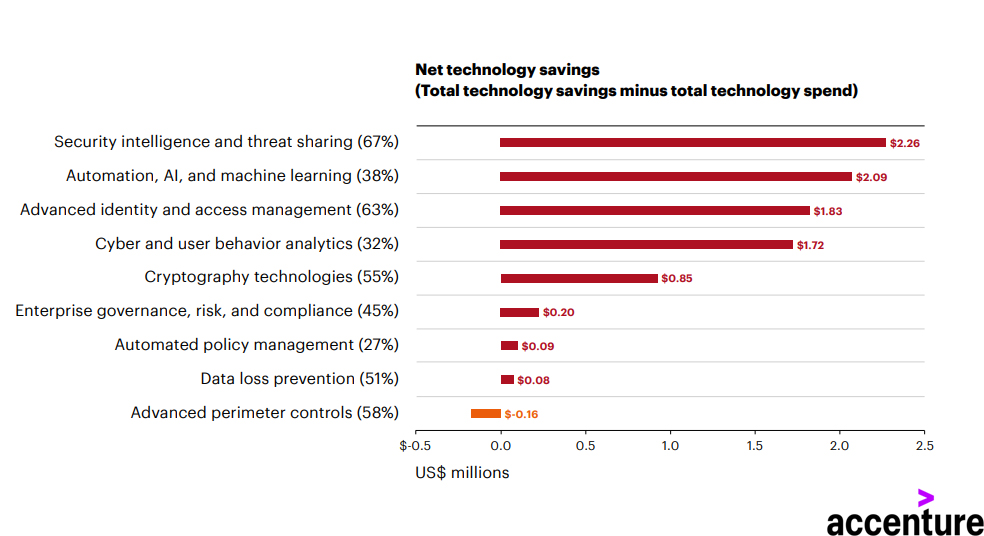
The Most Used Security Technologies With Their Net Cost Saving That They Provide, 2019
All organizations could benefit from the reduction in cybercrime cost enabled by further investment in advanced identity and access management. Security intelligence and threat sharing is widely deployed by companies and provides the greatest cost savings when compared with the levels of spend. It is not only an important enabling technology for both discovery and …
Researches
The Cost of Cybercrime: Ninth Annual Cost of Cybercrime Research, 2019 | Accenture
Cybercriminals don’t stalk only the big companies, on the contrary, the smaller companies are softer targets and easier to penetrate. And, because a network breach can be so devastating to a business, every business should take proactive measures to protect its network and devices. The word cybersecurity is now a part of the daily news …
Indicators
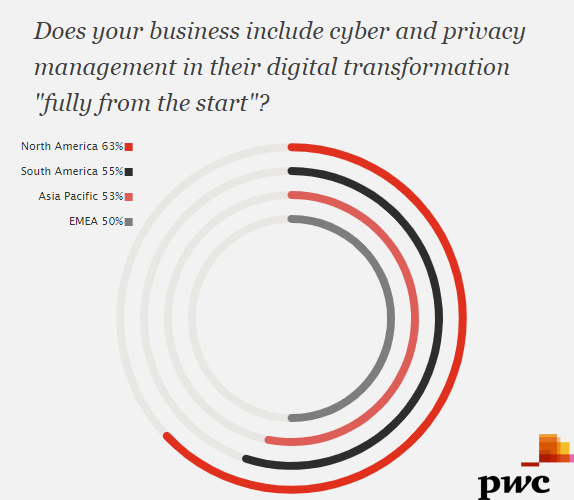
North America Region is Ranked as The Most With Businesses That Implement Cyber & Privacy Management in Their Digital Transformation With a Rate of 63%, 2018 | PWC
Organization & businesses are pursuing emerging technologies to develop new products, services, or ways of doing business while companies don’t always consider the emerging cyber security & privacy threats that could impact these systems after they’re implemented. Effective digital transformation requires a collaborative effort across departments involving partners, customers, and other stakeholders. Digital transformation imperatives …
Indicators
Instant Confirmations for Transactions is The Top Factor That Enhances The Customer’s Online Banking Experience & Security at a Rate of 72%, 2018 | Experian
Digital modernization gives traditional banks a second chance. A smart, enterprise-wide approach positions them to deepen customer satisfaction and loyalty, driving long-term relationships and profitability. Strong financial products and services are still essential. Digital banking is the move to online banking where banking services are delivered over the internet. The advantages for banks and customers …