Articles
Data Security in Digital Marketing: How To Avoid Common Breaches
The online business world is booming; that’s not in doubt. Retail e-commerce sales surpassed the USD$4.1 trillion mark in 2024 alone. That’s slightly more than the entire GDP of Italy and Canada combined. [1] However, as follows, every massive growth has bad actors. Cybercriminals have taken notice, and the digital sector is a prime target. …
Guides
Protect your business from phishing attacks in 7-steps | Backup Vault
In recent years, phishing attacks have become more frequent, signaling an increase in cybercrime profits. This success has allowed cybercriminals to invest more time and resources into making phishing attempts increasingly complex, convincing, and harder to detect. Given the numerous threats, it’s crucial to understand the key components of phishing scams and ensure your business …
Articles
Shielded Digital Assets: How to Mitigate Cyber Attacks
Assets come in many forms: cash and cash equivalents, properties, and vehicles, for example. Nowadays, many individuals and organizations also have digital assets. These may include design plans, cryptocurrencies, or information from a database. Unlike physical assets, digital ones are more challenging to secure. Hackers abound, and many people with cruel intentions seek to sell …
Guides
Addressing Cybersecurity in Your Business: A Guide for Entrepreneurs | BDC
Summary Why is Cybersecurity Important? It’s not a question of whether you will experience a cyber attack, but when it will happen. Discover the various cybersecurity challenges and how a proactive approach can provide you with significant advantages. Develop Your Cybersecurity Strategy Before making new investments, assess your existing measures and risks. Familiarize yourself with …
Articles
How to Implement Effective Online Security Measures for Your Organization
As human activities move from offline to online, the term “security” increasingly refers to cyberspace. Online security and privacy go hand-in-hand, often resulting from each other. Many companies have experienced an external attack or faced internal information security incidents at least once a year. The site of a small but growing demand project can easily …
News
Facebook Executives Spar with The Attorney General over Encryption and Privacy
It was a heated exchange on Monday, when Facebook executives and Attorney General William Barr argued over whether encryption messaging products should be open to law enforcement, or is it a violation of privacy. The situation looks to be escalating a standoff over privacy and policing. The executives overseeing Facebook’s WhatsApp and Messenger, Will Cathcart and …
Indicators
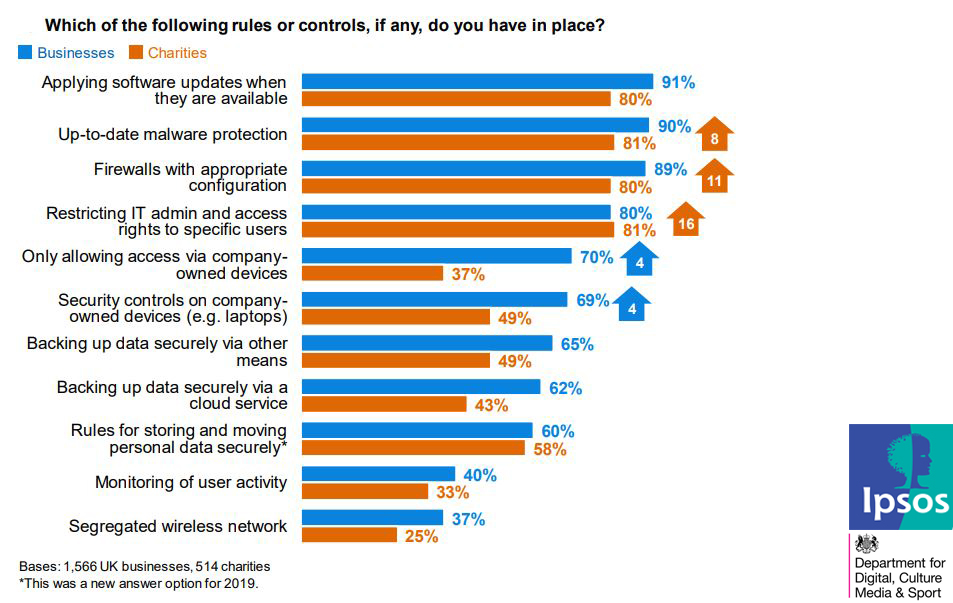
The Most Taken Actions by Businesses in Order of Preventing or Minimizing Cyber Security Risks, 2019
Cybersecurity is a huge issue from security breaches to computer hacks, companies are in a constant need to keep information confidential and safe. If there are loopholes in your security process, you are putting your product and customers data at risk. As large companies continue to get more serious about data security, small businesses are …