10 Code Signing Best Practices | Code Signing Store
Cyber Security
Code Signing Shields Your Hard-Earned Work…
Neglecting proper code signing and mishandling private keys can expose you to risks ranging from malware infiltrations to installation hitches for your clients. Continue reading to discover 10 practical code-signing best practices to maintain your organization’s security.
Every code segment, container, app, and executable you craft should prioritize security to prevent exploitation by malicious actors. Code signing is essential for affirming your digital identity and assuring users that your software is genuine and untampered.
However, the privilege of code signing carries significant responsibilities. Inadequate practices can severely harm your business and your clients. Hence, we have curated a list of best practices in code signing to help you avert potential issues.
But first, let’s address two critical queries:
Why is it crucial to sign your code correctly?
What are the consequences of neglecting code signing best practices?
The Importance of Correct Code Signing
Correctly executed, code signing offers a cryptographic seal of authenticity and integrity for your software, reassuring customers that the software genuinely originates from you and remains unchanged post-release.
Consequences of Neglecting Proper Management and Usage of Code Signing Keys
The NVIDIA incident in 2022 serves as a cautionary tale for what can happen when code signing keys are not securely managed. For those unfamiliar, the hacker group Lapsus$ exploited NVIDIA’s expired code signing certificates to sign and distribute malicious software.
Here are the risks you aim to mitigate by diligently managing your code signing process and keys:
1. Triggering warning messages that lead to poor installation experiences and potential customer loss.
2. Accidentally distributing malware under your reputable brand.
3. Enabling cyberattacks on your customers and end users via compromised software.
In essence, neglecting code signing best practices leaves you vulnerable and without recourse.
Before diving into the 10 code signing best practices you can apply immediately, let’s cover some preparatory steps.
Preparations Before Commencing Software Signing
1. Choose the Appropriate Code Signing Certificate for Your Needs
Selecting a suitable certificate tops our list of best practices because it’s indispensable for signing your software. There are primarily two types of code-signing certificates:
1. Organization Validation (OV) Code Signing Certificates:
Ideal for organizations seeking to certify their identity in their code cost-effectively. These certificates help eliminate basic warning messages like Windows’ “unknown publisher” alert during software installation.
2. Extended Validation (EV) Code Signing Certificates:
These offer the highest level of validation and are necessary for specific scenarios, such as certain Windows driver signing requirements or to bypass Windows SmartScreen alerts. Acquiring an EV certificate involves a thorough review of the requesting company, including its operational history and standing. Due to the extensive verification process and the physical hardware security tokens they’re issued on, EV certificates are more expensive than OV certificates.
Starting June 1, 2023, all OV certificates must also be stored on physical tokens or in Hardware Security Modules (HSMs) to comply with new industry standards.
What about individual developers not associated with a company? There’s an Individual Validation (IV) Code Signing Certificate option, akin to an OV certificate, requiring a personal identity verification process. This process includes:
– A face-to-face authentication with a notarized signature.
– Two forms of identity proof (like a government-issued ID or passport).
– Financial documentation (e.g., bank or credit card statement).
– Non-financial identity proof (e.g., tax or utility bill).
Note, that not all Certificate Authorities (CAs) offer IV certificates. Evaluate your specific needs and compare options to select the right certificate for your projects.
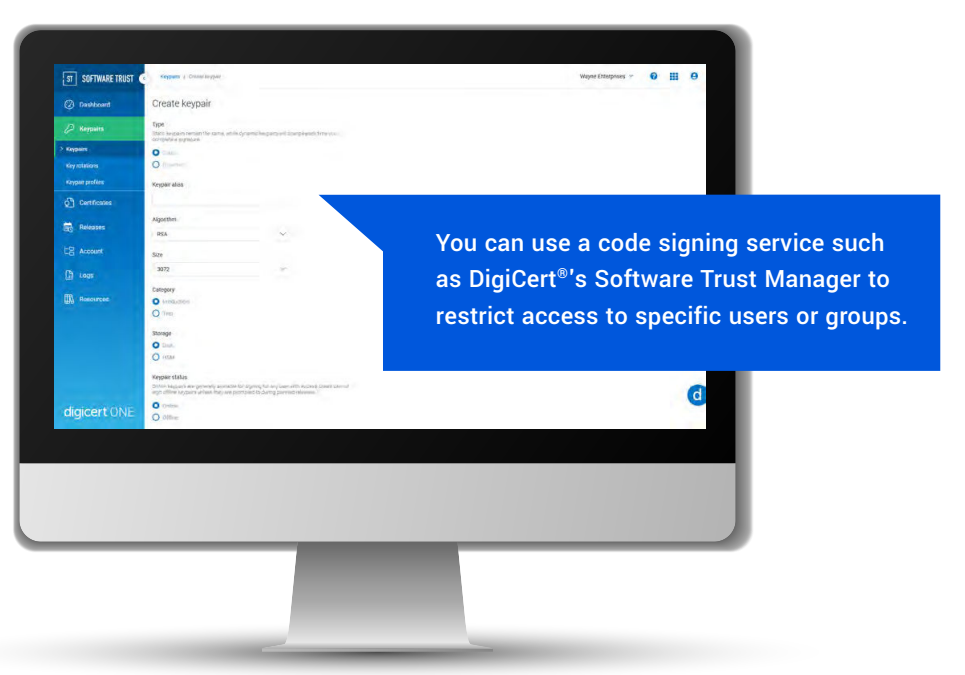
2. Maintain Strict Control Over Certificate and Key Issuance and Usage
A crucial practice in code signing extends beyond the signing procedure itself to the management of certificate and key issuance. It’s vital that not just anyone in your organization has the autonomy to request certificates or generate keys indiscriminately. Otherwise, tracking who initiated which certificate and the locations of the corresponding private keys—including potential unauthorized sharing—becomes a formidable challenge.
The foundation of the trust inherent in software signing is predicated on stringent oversight of access to private keys. This principle is equally critical in the broader context of Public Key Infrastructure (PKI), the cornerstone of online security. Certain solutions, such as DigiCert®’s Software Trust Manager (STM), offer mechanisms to regulate which individuals or groups are authorized to sign code.
Compromising this trust by neglecting to supervise who can create, access, and utilize your certificates and keys essentially undermines the integrity of your organization.
Research by Privitar indicates that approximately 25% of consumers cease interactions with businesses following data breaches. Considering this, imagine the consumer response to encountering unsigned malware disguised as your software, or installing software you’ve signed, not realizing it’s been tampered with to include malicious code. These scenarios represent both logistical and security catastrophes that are imperative to avoid.
Unlock the full potential of secure coding practices! Continue reading the guide now. Secure your code, protect your reputation, and enhance user trust. Click here to access the complete guide and elevate your security strategy today!
The Table of Contents of “10 Code Signing Best Practices” Guide:
- What You Should Do Before You Start Signing Your Software
- Best Practices to Follow When Actually Signing Your Code
- Why Code Signing Is a Must
- Simplify Your Code Signing Processes with DigiCert®
- Software Trust Manager
Number of Pages:
- 11 pages
Pricing:
- Free
Warning: Undefined array key "sidebar_ads" in /home/dmc/public_html/wp-content/themes/DMC/functions/helpers.php on line 824






